One of the questions most frequently asked by customers and prospective customers is the security and privacy level of our solutions. Learn more about this important topic.
Location-based data is actually sensitive information that must not be dealt with lightly. However, many concerns and fears are quickly weakened by looking at the technical details more closely.
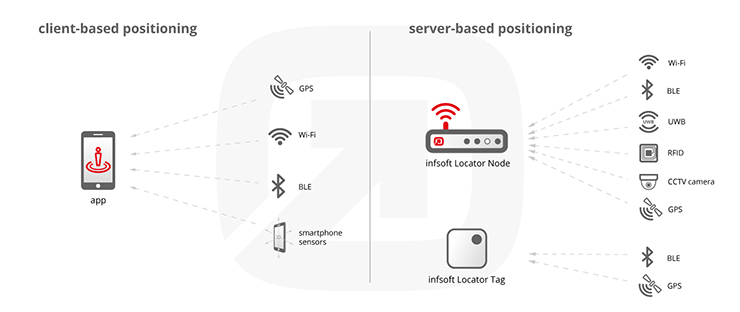
DATA PROTECTION IN CLIENT-BASED INDOOR POSITIONING SETTINGS
Client-based indoor positioning with beacons or WiFi, as used for indoor navigation, is basically extremely safe for the user and does not restrict privacy. In client-based settings, the location is determined directly on the user’s smartphone without further communication with a server. The data are not passed on or evaluated.
Additionally, beacons are no storage media on which personal data are kept. They only contain certain key figures by means of which they can be assigned, differentiated and parameterized. For example, it is completely without risk to use beacons for indoor navigation in sensitive environments such as hospitals. The beacon will never store details from the health records or other personal data.
The infsoft LocAware platform® works cloud-based and is highly fail-safe and powerful. If the customer wishes for it, we can use cloud servers in Europe.
DATA PROTECTION IN SERVER-BASED INDOOR POSITIONING SETTINGS
In the case of server-based applications such as anonymous tracking and analysis solutions, UIDs (unique ID of the mobile or beacon), RSSI (signal strength measured between receiver and telephone/beacon) and timestamp (time of activities) are transferred to the server by infsoft Locator Nodes. The MAC address identifies a single mobile telephone or a particular beacon. In anonymous applications, however, no person reference is made. Using a hash algorithm (SHA-1), MAC addresses of all device classes are reused as anonymous device ID in the systems in a non-reversible process. A conclusion to the original MAC address of the device is thus no longer possible. The smartphones of most manufacturers are already doing this (“MAC randomization”).
CAN A BEACON NETWORK BE “HIJACKED”?
A further concern of many companies is that other companies could “hijack” their beacon infrastructure and use it for themselves. For example, it might be possible that an unprotected beacon network of an airport operator is used by a shop operator or car hire provider for its own indoor navigation. This can be prevented by using a simple “rolling ID” method. The IDs for the unambiguous identification of the beacons are automatically switched. Only the operator of the beacon network has the appropriate “key” to decode this.
NO SIGNAL DISTURBANCES CAUSED BY BEACONS
Bluetooth beacons normally do not affect other radio networks due to interference, and sensitive devices such as those in the medical field are not affected by them. If you install beacons in a room with a lot of WiFi signals (for example at a trade show), interferences can occur as BLE and WiFi share the same frequency range (2.4 GHz). However, the problem can be easily circumvented by proper configuration.
INDOOR POSITIONING MADE SAFE
Indoor positioning can be made very safe by some simple measures. Modern cloud infrastructure helps. Talk to our experts about your questions and concerns!
Learn more about the basics of indoor positioning.